We're a team of two software developers located in the Midwest working to solve common issues we've seen in the K-12 space.
Our goal is to address exploits students use to circumvent web filtering programs. We noticed in early 2023 that many districts are dealing with this problem and that none of the big filters were providing good solutions. For example, proxies are a large issue, and most filter extensions only use a basic blacklist system where a URL goes in and true/false comes out—this obviously doesn't scale well with the number of clones students produce. We wanted to work on a more dynamic system for proxies and other exploits.
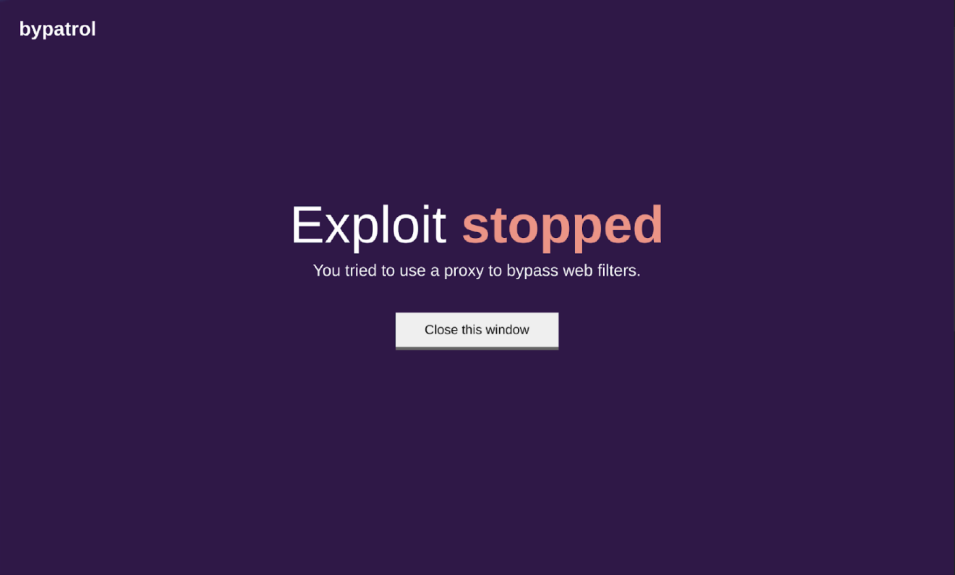
If a student were to use a proxy, for example, the offending tab or tabs would be closed, and an informative popup would show telling them why they have been blocked (shown here).
This process applies to a number of exploits.
When a student is in the process of using one or attempting to use one, Bypatrol will block it and the popup will be shown.
If you have any additional questions about Bypatrol's functionality, feel free to contact us.
Chromebook exploits that are commonly used in K-12 districts include cloned proxies, WebView exploits (a way of opening browsers inside Chrome apps), and cookie overloading. These allow students to completely bypass expensive filters meant to keep them safe inside and outside of school. Most filtering extensions don't bother to block or even acknowledge the existence of these exploits, which can be a large headache for sysadmins, as manually dealing with them is a time-consuming cat and mouse game. Bypatrol seeks to address this by automatically detecting and preventing the use of these exploits with our dedicated (and currently free) extension. In addition, our software also prevents miscellaneous exploits that don't directly affect filters but are still harmful, like WiFi password stealing exploits.
Get Bypatrol up and running on your district's Chromebooks in minutes.